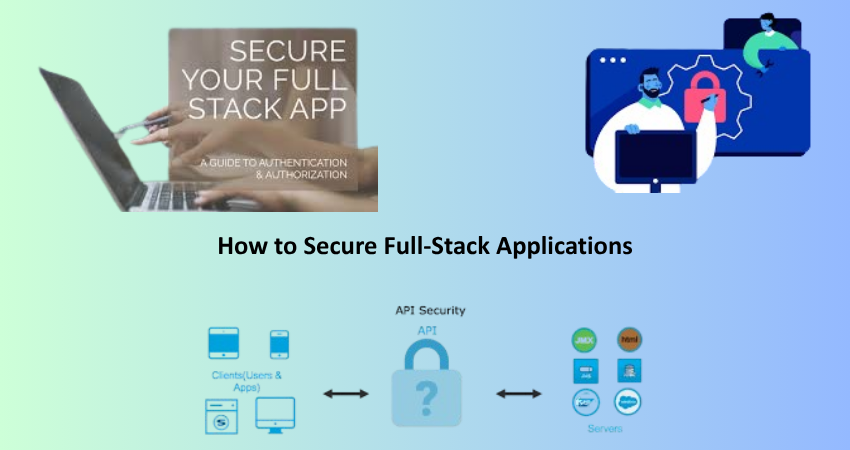
Introduction: The Importance of Full-Stack Security
Following recent trends, the security of full-stack applications is essential, with considerations that vulnerabilities at any layer have the potential to compromise the entire system. Full-stack applications range from the interface presentation layer to the background-working logic, databases, and APIs, as well as DevOps workflows. For every layer of complexity, the potential attack surface of the application increases, from which malicious actors would like to draw their scripts–injection attacks, authentication bypasses, data breaches, and server misconfiguration. Developers must indeed come to terms with the fact that security concerns span the entire application stack and are not solely the preserve of the backend engineers and IT administrators.
Any layer left unattended within the application stack is a potential risk. In other words, if user input is not sanitized on the client side, we may get XSS; if server-side validation fails to tackle malicious input, SQL injection may occur. Full-stack safe development follows a very proactive philosophy of defence and strictly holds best practices. As web applications are invoked to perform more and more kinds of sensitive information processing and key business transactions, it’s security that becomes a part of every phased development-from planning and design through deployment to maintenance.
Securing the Front-End: Best Practices for Client-Side Security
Input Validation and Content Sanitization
XSS, form tampering, and DOM-based injection are all examples of client-side attacks against which input validation and content sanitization can put up some contention. While these attacks are in some cases thwarted by default through the use of front-end frameworks such as React and Angular, much more needs to be done by the developers. User input should be treated as untrusted. Validate as thoroughly as possible before sending any data to the server. Sanitize everything that goes into the DOM, particularly user input, through HTML escaping or third-party libraries (i.e. DOMPurify). Validate through regex check the acceptable input for length and anything.
Attackers often use JavaScript UI to inject malicious scripts or tamper with form submissions. Any CSP headers set in conjunction to limit what sources of scripts are to be permitted will aid greatly in defusing XSS attacks. Also, avoid inline scripts as well as code that is dynamically generated and executed using either eval() or innerHTML since these often present opportunities for client-side exploits. An adequately secured front end acts as a robust first line of defense and reduces the burden on backend filtering mechanisms by filtering out obvious threats upfront.
Secure Handling of Sensitive Data in the UI
The front end quite often manages and exhibits sensitive user data, like authentication tokens, email addresses, or even credit card details. It is prone to revealing such information inadvertently through browser history, console logs, or local storages. Developers should strictly avoid putting all sensitive data like JWTs or session tokens into localStorage or sessionStorage since client-side scripts could access such data. Instead, have secured, HttpOnly cookies when possible to avoid access via JavaScript.
Another part is proper implementation of secure forms over HTTPS, prevention of browser autocomplete on sensitive fields, and error messages that reveal no internal detail. UI-level access control should be backed up with back-end validations as hiding buttons or pages on the front end does not make for a fool-proof way to secure access from clever attackers. Secure UI practices serve two important purposes, that is, to protect the user and lay the ground for an entire section of end-to-end secure application architecture.
Back-End Security: Building a Hardened Server-Side Foundation
Authentication and Authorization Mechanisms
Authentication and authorization are essential for security on the backend — authentication ensures verification of identity information, authorizing access to only permitted resources. Strong authentication protocols, such as MFA, OAuth 2.0, and OpenID Connect, can significantly enhance application cybersecurity. The use of conventional authentication techniques like plain text passwords and custom hashing algorithms must be avoided; on the contrary, much-broken encryption libraries like bcrypt, Argon2, and PBKDF2 should be implemented.
The authorization must be performed either by Role-based Access Control (RBAC) or Attribute-based Access Control (ABAC), and the permissions should be strictly enforced at the API and database levels. Access control should be implemented in the frontend, but never relied upon completely for defense. Throughout the system, countermeasures should be taken against privilege escalation or horizontal access attacks. JWT based systems must be securely signed and properly tested so as to not be misused, while setting up proper session expiration handling. Shortening the session time, setting IP restrictions, and keeping login anomalies will only serve to reinforce the authentication system.
Preventing Injection and Logic Attacks
Typically, injection attacks are regarded as the most hazardous and widespread threats against the back-end systems. SQL injection, command injection, but also NoSQL injection all have the potential to cause data breaches and an outright compromise of the system. Protecting against injection attacks means never interpolating user inputs directly into queries or commands. Instead, parameterized queries or ORM frameworks are to be utilized, ensuring inputs are always sanitized–for example, Sequelize for Node.js or Hibernate for Java.
Next to injections, one could logically call these also dangerous–flaws existing in the application code. An example of this includes using a predictable ID number within a URL with no access validation, allowing an attacker unauthorized access to protected resources. Conducting code reviews regularly, using static code analysis tools such as SonarQube, and performing security unit testing do help detect and remove this type of logic flaw during their developmental phase, avoiding exploitation. Development teams should be educated about typical OWASP vulnerabilities, making sure that they can embed security into their software from the start.
Database and API Security: Protecting the Data Layer
Secure Database Configuration and Access Control
Databases are basically the warehouses of sensitive information, and hence, a prime target for the attackers. The first point with which one can secure the database is closing down all default accounts, changing his port numbers, and enabling encryption for data both at rest and during transit. Privileges of the database user should be limited by the principle of least privilege-in fact, an application should not connect with administrative rights if it is not absolutely essential. It must sufficiently monitor and log all accesses for detection of any suspicion, and have automated alerts for unusual query patterns or failed login attempts.
Connection strings and credentials should be held securely as environment variables or secret management tools like HashiCorp Vault or AWS Secrets Manager. Do not hard code credentials in your codebase and avoid storing them in public repositories. It is better to update regularly and patch the database software over known vulnerabilities. Use firewall rules to limit access to the database from known IP ranges and VPNs only. The securing of the database infrastructure is as important as writing secure queries to protect sensitive data in the event when other layers get compromised.
API Rate Limiting and Authentication
API refers to the heart of full-stack applications, establishing communications between the front end and back end. API poorly secured denies data leakages, DDoS attack assaults, or unauthorized access. OAuth2 tokens, API Key, or a signed JWT should be put in place for API authentication as the first line of defense. Each API should enforce strict access control and role-based permissions to ensure that users can only interact with endpoints pertinent to their role.
Rate-limiting will be required to prevent any abuse or brute-force attempts. This is achievable through requests-per-IP or requests-per-token limiting with tools such as NGINX, AWS API Gateway, or Express middleware. In addition, input validation and output encoding will serve to protect your services from malicious payloads while working with rate-limiting functionality. Exposing internal endpoints, including debug APIs, should also be avoided. All-around API security would maintain your data layer’s security with the ability to offer service via the required uptime and performance.
DevOps and Deployment: Securing the Operational Pipeline
CI/CD Security and Dependency Management
Security prerequisites are to be analysed, at staging and production environments, to assure that only trusted codes will actually be pushed into production. Protect your CI/CD environments using access restrictions, SSH keys instead of passwords, OAuth tokens instead of passwords, and regular credential rotation. Use tools like Jenkins, GitHub Actions, or GitLab CI with minimal required privileges and sandboxed environments. Never expose secrets in logs or environment variables; keep them safe with secret management integrations.
Another major area required for CI/CD security is dependency management. Schedule regular scans of your codebase using tools like Snyk, Dependabot, or npm audit for the known vulnerable libraries. These packages are more likely to have serious vulnerabilities because they are outdated or rarely patched. Make scans part of the pipeline and prioritize them according to the severity of the risk. Keep a Software Bill of Materials (SBOM) to track all the third-party dependencies by which compliance with security standards can be ensured.
Infrastructure as Code and Container Security
The glory days of infrastructure as code (IaC) emphasizing tools like Terraform, CloudFormation, Ansible, et cetera, has enabled the status of your infrastructure configuration to become a part of the codebase. This implies that it should be treated with coincide rigor as for the rest of your codebase. Version control; peer review; static analysis should be carried to the IaC files. Further policies should be laid down to avert any misconfigurations, including misconfigurations such as open security groups, exposed ports, or overly permissive roles, to name a few. Such compliance can be automated with tools such as Checkov, TFLint, or Open Policy Agent.
Containers must be secured throughout their lifecycle. Work with minimal base images; scan for vulnerabilities frequently; and wherever possible, please do not run your containers as root. In this case, the Kubernetes orchestrator must have RBAC enabled, network policies defined, and secrets securely managed. Monitor container behavior with runtime security tools like Falco or Aqua Security. With the infrastructure and deployment practices secured, you make sure that if a weak point in any component is ever exploited, the overall stack remains resilient.
Conclusion: A Holistic Approach to Full-Stack Security
In a world where threats can suddenly appear from any layer, a piecemeal approach to securing full-stack applications is unsatisfactory. Security checks must therefore be included at all layers from UI to database, from API level to infrastructure. Candidly speaking, developers and DevOps teams must work together toward the common goals of enforcing strong authentication and input validation, handling data and deployment in a secure manner, and conducting thorough audits and security training. No tool or framework is going to give you 100% security. Then it’s really a strategy involving regular audits and a culture of security-first thinking.
Following the best practices in the industry would help by minimizing the risks and securing the user data and application itself. Security must grow along with the evolving threats. A security-first attitude not only secures your application but also gains user trust, compliance, and ultimately continued success in the digital world.